What Is Access Control System

Are you in control of deciding who gets access into your company and its resources? Whether you are a small scale business or a larger enterprise, having an access control system is imperative for your organization. According to markets and markets, the access control market is projected to grow from $10.4 billion in 2024 to $15.2 billion by 2029, with a CAGR of 7.8%. But first, it's essential to understand – What is access control system and how it can secure your business.
With the growing concerns of security across sectors of businesses, educational institutions, healthcare and government facilities, the need for stringent and unwavering security measures has never been more critical. In today's scenario, we deal with sensitive data, unrecognized physical and virtual intrusions, cyber insecurities, and other delicate yet crucial challenges.
In the face of today's advanced technology integrated infrastructures the conventional systems such as the locks and keys, manual check ins, security patrols neither fit nor are reliable anymore. We cannot depend on traditional security systems as they were made for more simpler times rather than today's sophisticated technology integrated environment.
What Is an Access Control System?
An access control system determines who gets to access your resources whether it be physical or cyber facets of your company. It strategically monitors and controls the individuals allowed to enter your facilities, ensuring approved entries and enhanced workplace security. Access control systems have the ability to differentiate between unauthorized and authorized attempts based on set and customizable criteria.
Access control is simply a tool that is inclined towards providing workplace security by protecting your company’s sensitive data, assets and establishments by ensuring that only trusted users get to access them.

Primarily there are two types of access control, let's understand each one of them in detail:
Primary Types of Access Control
1. Physical Access Control System
The physical access control system regulates and oversees others' access to physical or off-network sites such as offices, institutions, hospitals and other facilities. Its primary function is to recognize sneaky or unpermitted entries through various measures such as biometrics, key cards or visitor management systems to stop such unauthorized admittance. These systems are mostly installed at the entrance of offices, hospitals, government organizations etc to perform its diligence at the gateway itself.
2. Logical Access Control System
Logical access control system on the other side regulates access to digital resources and systems. It restricts the access rights to files and applications based on user authentication and authorization. Logical access control systems use an access control list (ACL) to specify the users that can receive access to certain files. User authentication methods, such as passwords, verification methods or fingerprint scans, verify the person before granting access. These methods work in accordance to ensure that only right people get to access digital data and resources.
Why Access Control Is Crucial for Office Security?
In today's complex digital era our offices are no longer vulnerable only to ordinary or simple attacks, rather we are in the radar of more sophisticated and deceptive attacks. With digitalization and integration of technologies we now have a list of potential threats both physical and cyber such as unauthorized entry, theft, tampering, data breaches, phishing, and insider threats and much more. Neglecting a proper security plan increases your vulnerability to both physical and cyber attacks.
Access control systems serve as a solution that not only identifies potential threats but also effectively addresses them. Verizon, 2020 report suggests that 70% of attacks such as data breaches are caused by external parties. The incidents rose from 2,013 in 2019 to 3,950 in 2020—an increase of nearly 95%. By preventing unauthorized or unrecognized access to your physical and virtual resources, access control systems reduce the possibility of such attacks.
Benefits of Access Control Systems
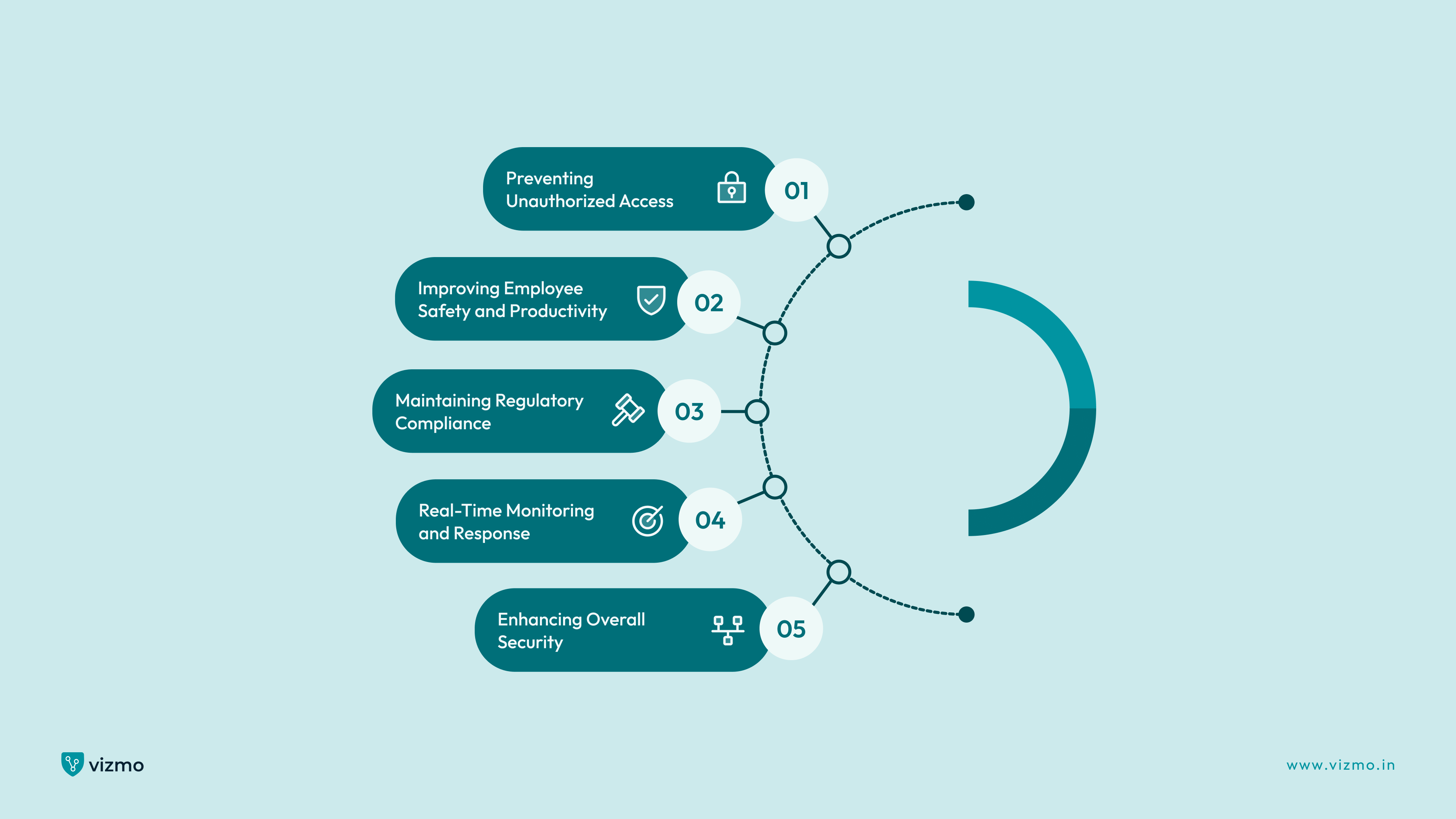
1. Preventing Unauthorized Access
The primary role of access control systems is to create a barrier in front of entities that have confidential information, people and assets. The access control system protects your organization and data and people from breaches, theft, physical harm, vandalism and other potential threats by making decisions related to authorization and providing access. Additionally, they provide valuable audit trails and real-time monitoring, enhancing your ability to track and respond to security incidents effectively.
2. Improving Employee Safety and Productivity
Employees tend to perform better in environments they feel safe and secure in. It is your responsibility as a company to enforce strategic security implementations to both protect your data as well as your people. Access control systems are the way to achieve this, they restrict entry to all the areas you wouldn't want anyone to reach without your knowledge, as a result securing both your data and employees. Additionally, knowing that their workplace is protected from potential threats allows employees to focus on their work without distraction, further boosting overall productivity.
3. Ensuring Compliance with Regulations
Using access control systems helps companies adhere to several compliance regulations. The access control systems help organizations maintain detailed logs of access events, recording who accessed what information and when. These logs are useful during audits proving that the company is following the right security measures and required regulations. Access control systems can facilitate the enforcement of data protection policies and industry standards, ensuring that your organization remains compliant and avoids potential legal or financial penalties.
4. Real-Time Monitoring and Response
During risks and hazards, access control systems can trigger real-time alerts and execute emergency evacuation protocols. They monitor access in real-time, detect risks, and respond quickly to incidents, ensuring a safe and efficient evacuation process. This proactive approach helps maintain security and manage emergencies effectively, contributing to a safer work environment. This proactive approach not only enhances overall security but also ensures that your organization can manage and mitigate emergency situations effectively, contributing to a safer and more secure work environment.
5. Enhancing Overall Security
A good access control system integrates with other security systems, such as video surveillance, alarm systems, motion sensors, and cyber security protocols. This integration provides a comprehensive security framework that enhances your overall security posture. By consolidating multiple security measures, access control systems offer a more robust and cohesive approach to safeguarding your organization. This proactive approach not only enhances overall security but also ensures that your organization can manage and mitigate emergency situations effectively, contributing to a safer and more secure work environment.
How Does Access Control System Work?
The access control system operates based on pre-established criteria that include unique PINs, usernames, passwords, and other forms of identification. Upon analyzing the form of identification, the access control system determines whether the access should be granted to the user. Based on the unique credentials associated with their identifier, the access control system even decides the timing and the amount of access to be granted.
The access control system follows a three-step process: identification, authentication, and authorization.
Identification
This is the very first step that an access control system performs. The access control system attempts to identify the individual seeking access by verifying their unique credentials or identification. This ensures that only authorized individuals can proceed further. The different forms of identification factors can be keycards, biometric data like a fingerprint or facial recognition, or a personal identification number (PIN).
Authentication
Upon receiving identification data, the access control system tries to process it against its database to verify the individual. This helps the access control system determine whether the person trying to access is legitimate or not. To enhance security, authentication can be extended to include two-factor authentication (2FA) or three-factor authentication (3FA), adding extra layers of verification.
Authorization
Once authentication is successful, the system checks whether the individual has the appropriate permissions to access the requested area or resource. If the person is authorized, access is granted, otherwise, it is denied. This ensures that only individuals with appropriate clearance can enter restricted areas or access sensitive information, completing the whole process.
Components of an Access Control System
To carry out the three step process of identification, authentication and authorization the access control system interacts with its various components:
1. Credentials
Credentials are digital or physical means by which individuals verify their identity to receive access to systems and physical spaces. Physical credentials can include keys, cards, key fobs and ID badges. Digital credentials include passwords, smart cards, biometric data, pins and more.
2. Readers
Readers are the devices that read the credentials of people trying to receive access and authenticate them. The reader has the ability to communicate with access control systems as the reader sends the credential information to the control panel to verify the validity of credentials. The reader can authorize or deny access based on analyzing the verified credentials.
3. Control Panels
Control panels receive credentials data from the readers to check it against the database present in the access control systems. They are responsible for processing the information received from the readers and making access control decisions. According to the validity of the credentials the control panel sends a signal to grant access to the credential holder. Control panels also work in compliance to keep access logs for monitoring and auditing purposes.
4. Access Control Servers
Access control servers communicate with the access panels to administer and monitor access control operations. They maintain a preset database, according to which the system is able to make access-granting decisions. Access control servers integrate with other security systems, such as video surveillance or alarm systems, to enhance the overall security posture of the organization.
Types of Access Control Systems
Now that we have a clear understanding of how an access control system functions, let's explore the various types of access control systems that are out there.
1. Discretionary Access Control (DAC)
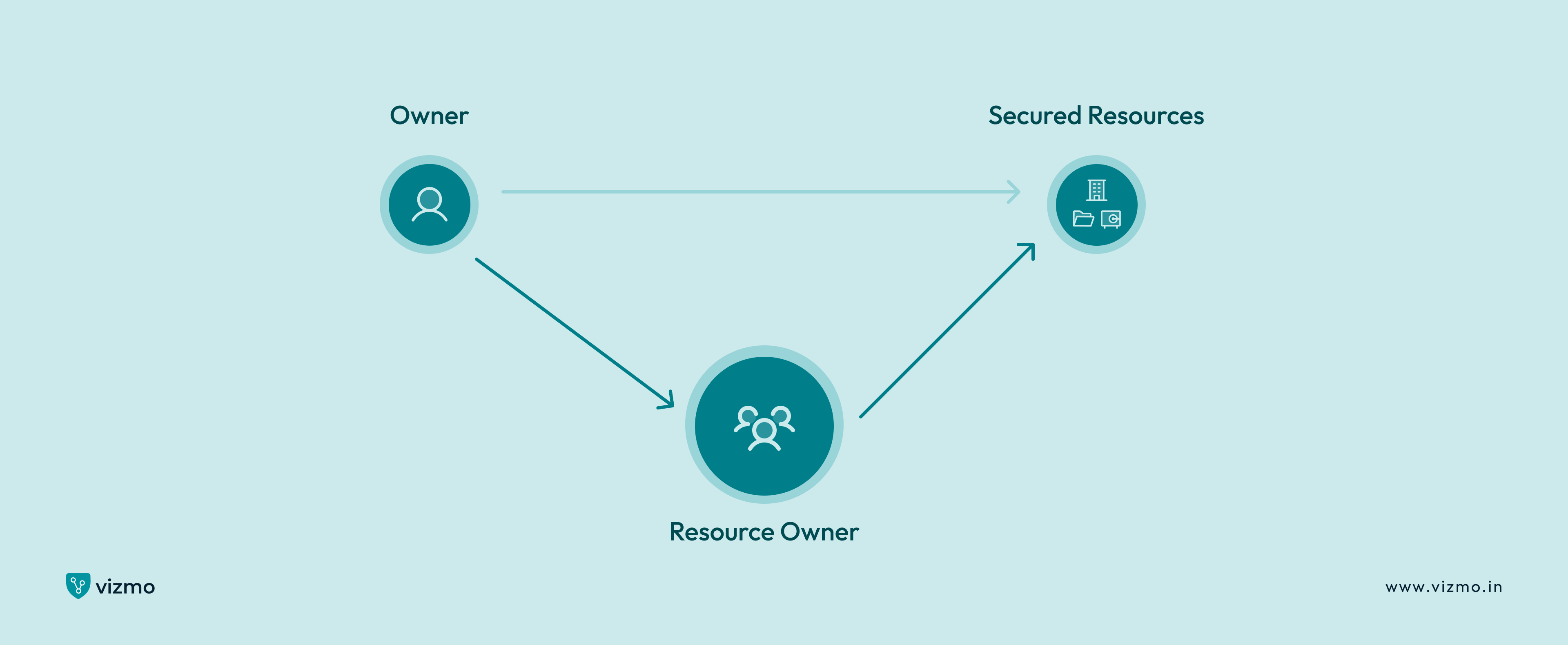
Discretionary access control is the simplest and the most flexible control model among the different types of access control systems. In a discretionary access control system, any person with the accurate credentials can obtain access without having to take permission from the administrators.
After access being granted, each user receives the same level of control over the resources. The owner or administrator of the resource can modify rights of access according to their own. This type of model works best for multi-unit residences or businesses with multiple managers. However, individuals with credentials may be able to gain access without proper oversight.
2. Mandatory Access Control (MAC)
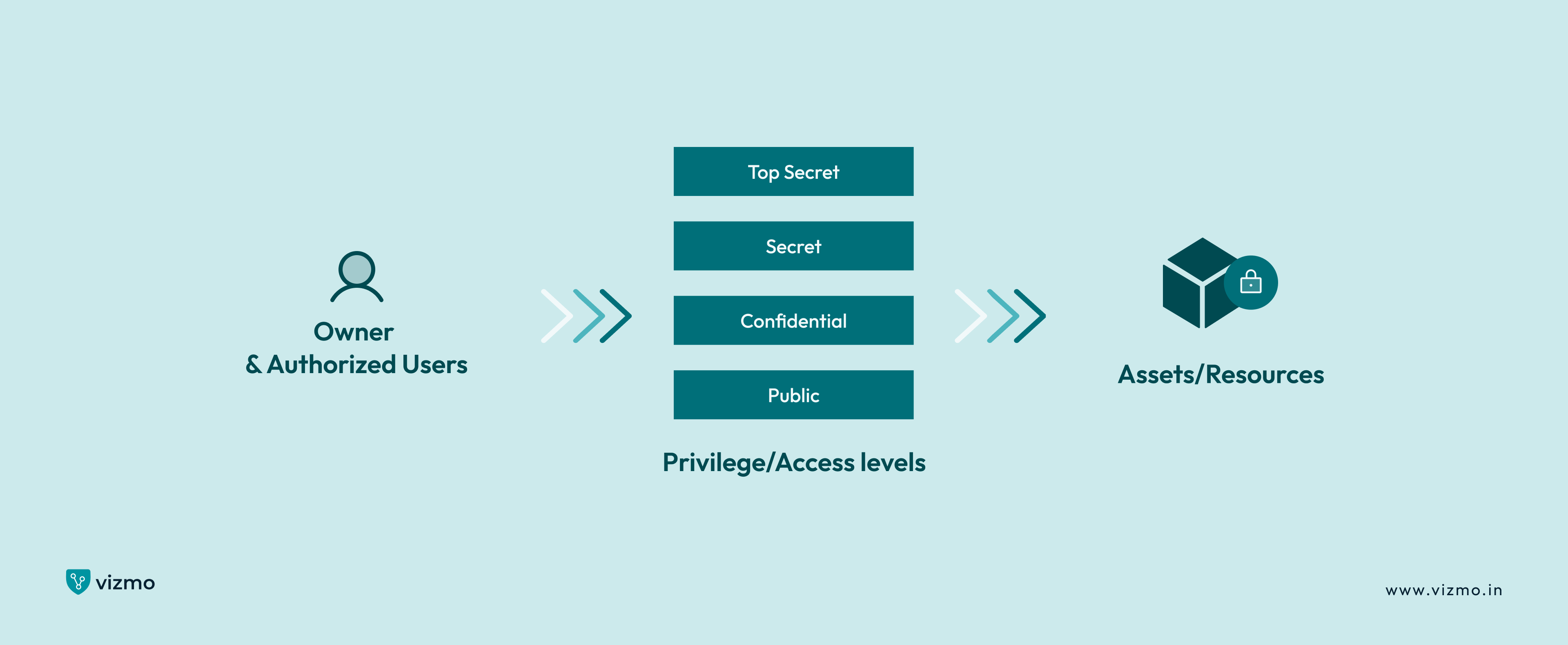
In contrast to the discretionary access model, the mandatory access model is the most restrictive of all. The access in the mandatory access control model can only be granted by the administrators or the people who control the system. The administrator or the owner has the ability to decide the level of access that can be granted and modify permissions according to classifications.
Mandatory access control best fits for businesses or organizations that prioritize maximum security, with credentials confined to a single, high-level operator. The only downside to such a high-level access control system is that implementation can be challenging unless you partner with a reliable provider.
3. Role-based Access Control (RBAC)
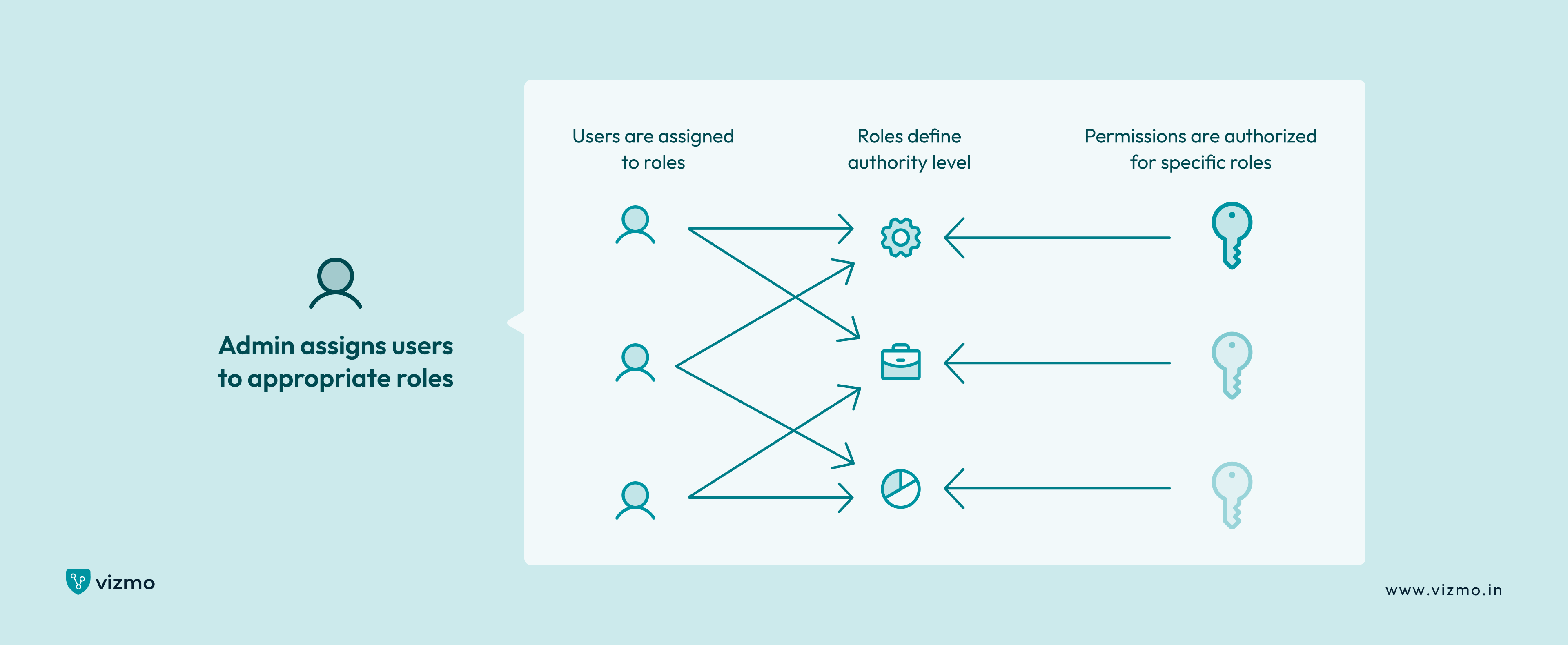
Role-based access model as the name suggests, distributes the level of access among employees or people according to their roles. The model is also known as the non- discretionary access model and is one of the most commonly implemented access control systems. The administrators have the ability to assign the level of access to be provided according to the roles such as manager, employee, IT administrator etc.
This type of access model can be seen in both commercial and residential properties. However, in large organizations, it can be challenging for the administrator or the owner to manage providing the right level of access to different people of the organization or area.
Typical Uses of Access Control Systems
An access control system comes as a security and efficiency solution, not only to corporate facilities but to other organizations and industries as well. Prioritizing safety isn’t just a crucial intent of businesses, it is a paramount necessity for healthcare facilities, educational institutions, and government buildings as well. An access control system is generally useful in different industries in various ways such as:
Government data centers: Government data centers house highly sensitive and classified information critical to national security. Access control systems ensure that only authorized personnel can enter these facilities, protecting against unauthorized access and potential data breaches. By implementing multi-factor authentication and biometric access, the security of these critical areas is further strengthened.
Corporate offices: In corporate environments, access control systems help manage who can enter specific areas, such as executive offices, server rooms, and storage facilities. By restricting access based on role or department, businesses can protect intellectual property, confidential documents, and other valuable assets.
These systems also streamline on-boarding and off-boarding processes by automating access permissions, reducing the risk of human error, and ensuring that former employees no longer have access to critical areas. Additionally, access logs can provide valuable insights into employee movement and activity within the office, further enhancing security measures.
Medical facilities: In healthcare environments, access control is crucial for maintaining patient privacy and ensuring that only authorized medical personnel can access sensitive areas like treatment rooms, pharmacies, and patient records. By controlling access to these areas, hospitals, doctors' offices, and health insurance companies comply with regulations and improve overall patient care.
Banks and financial institutions: Banks rely on access control systems to protect vaults, ATMs, and secure rooms where transactions and sensitive financial information are handled. These systems ensure that only authorized employees can access these critical areas, reducing the risk of fraud, theft, and unauthorized transactions.
Additionally, access control systems can integrate with surveillance and alarm systems, providing a comprehensive security solution that quickly responds to potential threats. This level of security is essential for maintaining trust with customers and ensuring regulatory compliance in the financial industry.
Law enforcement facilities: Access control systems in law enforcement facilities are essential for maintaining the integrity of evidence rooms, detention areas, and administrative offices. By controlling who can access these areas, these systems help prevent tampering, unauthorized access, and breaches of confidential information.
Hotels: In the hospitality industry, access control systems help manage guest access to rooms, amenities, and facilities, ensuring that only paying guests can use them. Additionally, they secure staff-only areas like kitchens, storage rooms, and administrative offices, keeping hotel operations smooth and secure.
Educational institutions: Schools, colleges, and universities use access control systems to protect students, staff, and visitors by regulating who can enter classrooms, dormitories, labs, and administrative buildings. These systems help prevent unauthorized access, ensuring a safer learning environment.
Gyms and fitness centers: Gyms and fitness centers use access control systems to regulate member entry, ensuring that only paying members can access workout areas, locker rooms, and other facilities. These systems also help secure personal belongings, manage facility usage efficiently, and provide detailed insights into member activity patterns, enabling gyms to optimize their services and maintain a secure environment for all the gym members.
Residential areas: In residential areas like apartment complexes and gated communities, access control systems manage entry to buildings, parking areas, and shared facilities like pools or gyms. This ensures that only residents and authorized visitors can access these spaces, enhancing the safety and security of the living environment.
Installing Access Control System
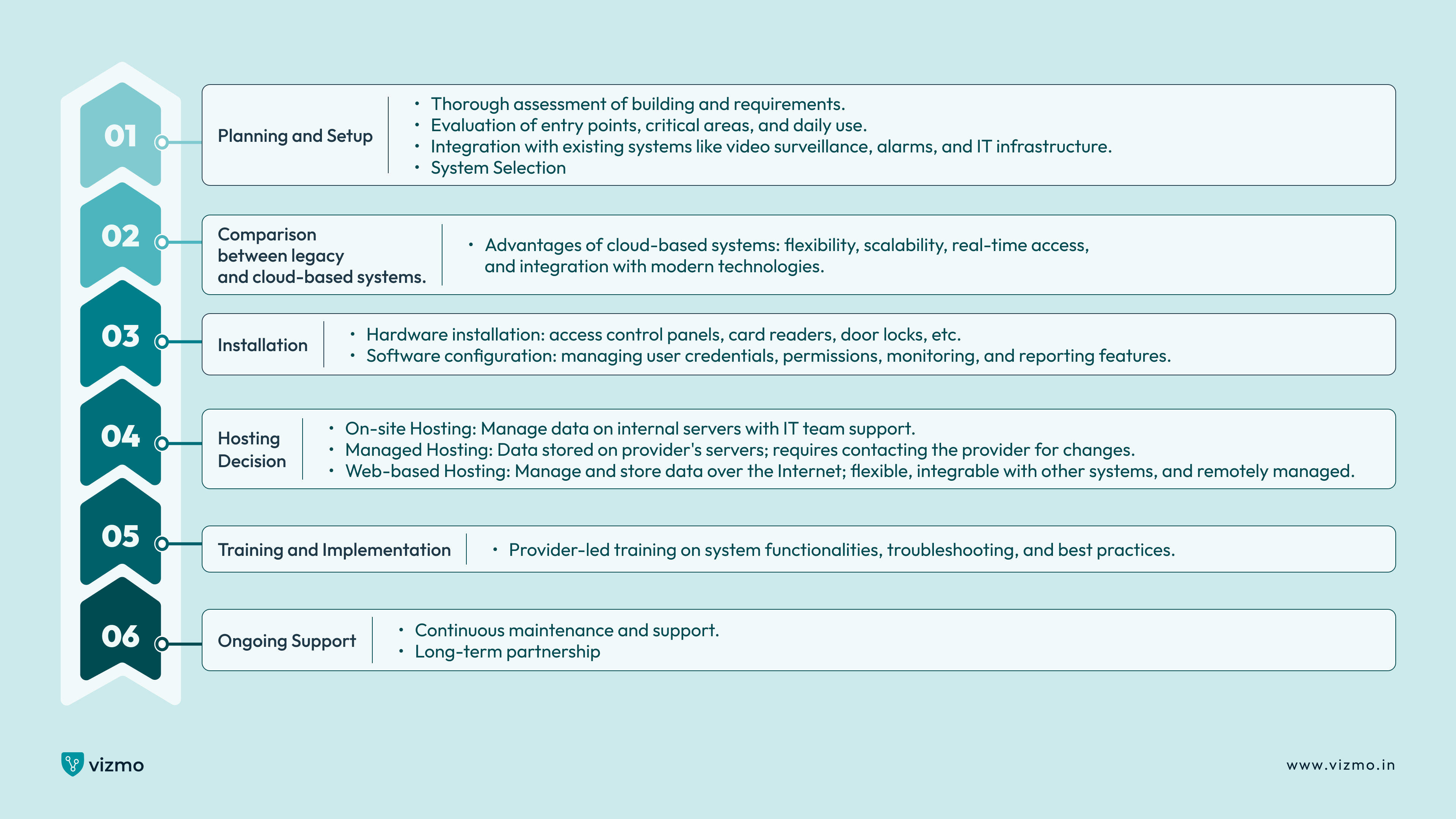
It is important to select a professional provider for installing your access control system. Access control systems can be tailored to your particular situation and infrastructure. You need a provider that understands your specific needs and is there with you with your whole access control journey, even after the installation, not just the beginning.
1. Planning and Setup
The provider will examine your building and conduct a thorough assessment of your requirements. This involves evaluating entry points, identifying critical areas, and understanding how the access control system will be used daily. It is crucial to plan how the access control system will be installed to ensure seamless integration with existing systems, such as video surveillance, alarm systems, and IT infrastructure. This integration creates a cohesive security environment, enhancing overall efficiency and protection while allowing for centralized management and monitoring.
2. System Selection
Between legacy and cloud-based options, it is mostly suggested to go with cloud-based systems. A legacy-based access system works on traditional outdated methods like static passwords or simple PIN codes. These systems may not support advanced features like biometric authentication or remote access. A cloud-based solution on the other hand would let you store data and run software on remote servers accessible over the internet, offering more flexibility, scalability, and ease of management.
Cloud-based systems can be updated more easily, integrate with other modern technologies, and provide real-time access to security controls and monitoring from anywhere, making them a better choice for managing your organization’s security needs.
3. Installation
The installation process would include both hardware installation and software configuration. Hardware setup would include your provider to install physical elements such as access control panels, card readers, door locks etc. Later the provider would integrate the system with software configuration to let you manage user credentials and permissions.
This integration also includes setting up monitoring and reporting features, enabling real-time tracking and audit trails of all access events. Proper installation ensures a seamless operation, providing robust security and easy management of your access control system.
4. Hosting decision
When setting up your access control system, choose whether to host it internally, externally, or within your company's network. Decide if your IT team will manage it, or if an external manager will handle it. Each option has its own impact on control, security, and maintenance.
You can select one of these hosting options:
On-site hosting: You can choose to manage your access control system internally on your site. This allows you to manage data on your own servers and to change access rules and permissions directly with the help of your IT teams. On-site hosting offers greater control over security and data management, as everything is contained within your organization's infrastructure. However, it may require more resources for maintenance and upgrades.
Managed hosting: This option would let you store your data on the servers of your providers. This is a cost-effective solution, although it requires you to frequently contact your provider for every change you would want to your system’s data. Managed hosting reduces the burden on your internal IT staff, as the provider handles updates, backups, and security patches. However, you may face limitations in customization and responsiveness when immediate changes are needed.
Web-based hosting: web-based hosting for access control systems is one of the best hosting solutions among the options. It lets you manage and store data over your Internet network. Web-based hosting is flexible, it can be integrated with other systems and be remotely managed making it the most reliable option for businesses with many outlets. Additionally, it allows for real-time monitoring and access from anywhere, making it ideal for companies with multiple locations or remote workforce.
5. Training and Implementation
Seek proper training from your provider to ensure a smooth transition to start managing your access control system. This training should cover system functionalities, troubleshooting, and best practices for maintaining security. Proper implementation and ongoing support will empower your team to confidently handle the system, ensuring that it operates effectively and meets your organization’s security needs.
6. Ongoing Support
It's better to select a provider that stays with you ensuring proper maintenance and support. Handling an access control system can be challenging and with a reliable supporter like Vizmo, you can stay assured of seamless management and expert assistance.
A trusted provider will not only help you implement the system effectively but will also offer ongoing updates and technical support, adapting to your evolving security needs. This long-term partnership ensures that your access control system remains robust, up-to-date, and capable of protecting your organization as it grows.
Final Thoughts
Most businesses are choosing to upgrade from traditional non-digital tools or manual processes to digital tools and technologies to manage their business operations. Switching to automated solutions enhances your business' operational efficiency ensuring safety and reliability at the same time. In today’s scenario implementing an access control system not only means to speed up your working pace but also to reinforce security of your business both on the physical and digital out-front.
Vizmo offers an end-to-end security solution for your specific needs. With expertise in workplace management and security solutions, we guide you through explaining and implementing the right access control system for your infrastructure.
Moreover, we assess your site, looking to provide you with best integration opportunities with your existing systems. Book a Demo With Vizmo to get started with your own access control system.

