Types of Access Control Systems

An access control system is a strategic approach to protecting your workplace, organization, or resources from unauthorized access and potential security threats. These systems keep track of who enters and exits, preventing unauthorized access and reducing theft and accidents.
According to access control trends and highlights 2024-2036, the access control market was valued at $10.69 billion in 2023 and is expected to grow to $29.72 billion by 2036, with an annual growth rate of about 8.3%. In 2024, the market size is projected to be $11.48 billion.
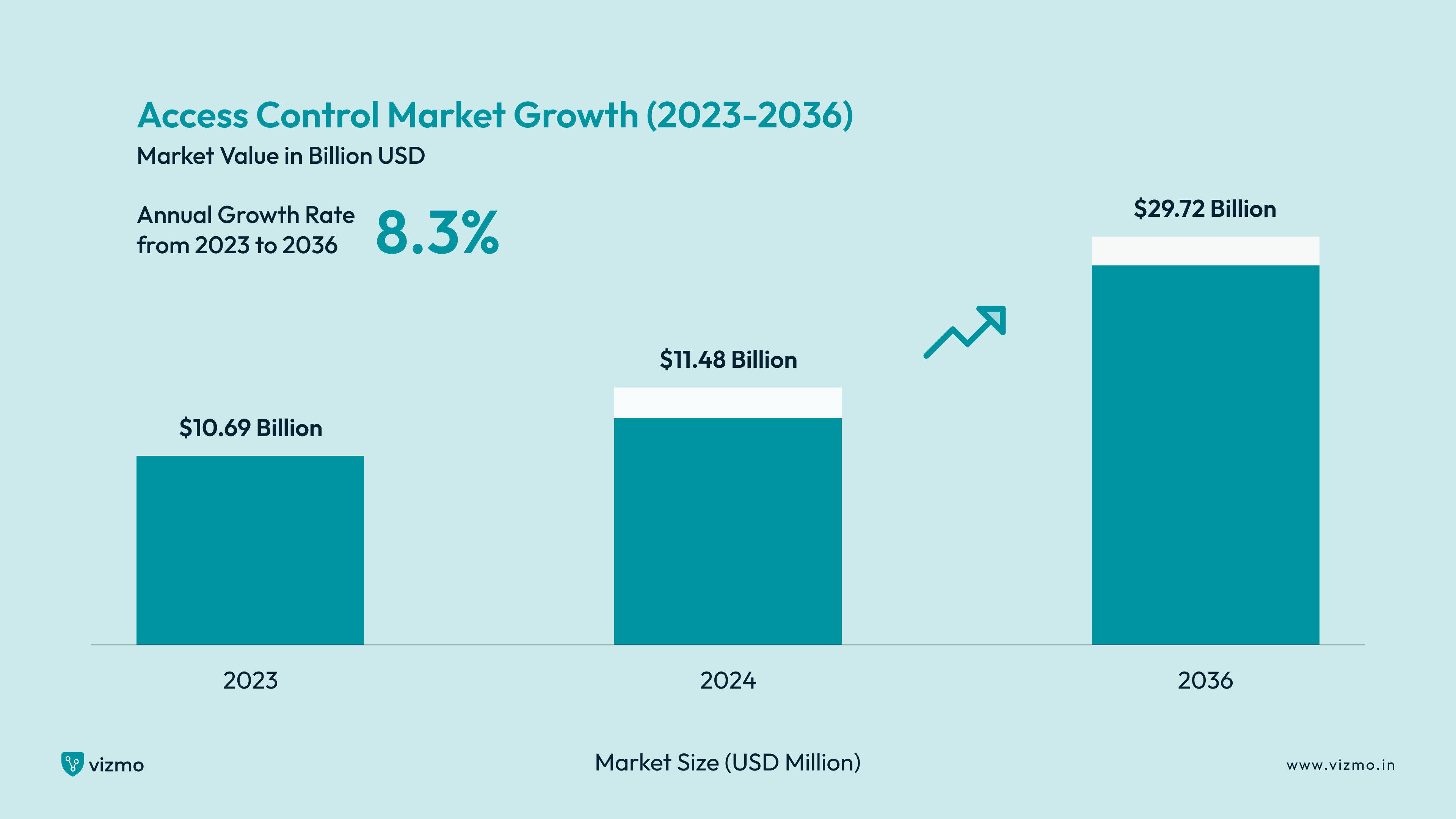
The report suggested that the evident growth of access control systems is due to the increasing number of thefts in homes, businesses and other facilities. Additionally, the growth of the access control market is also driven by the increasing number of IoT devices and the rise in cyber crimes.
While this highlights the importance of implementing access control systems, choosing the right model among the different types of access control systems for your specific needs requires careful, informed decision-making.
Types of Access Control Systems
Access control systems play an important role in regulating access to certain resources, whether it be physical, logical, or network-based access. To give you a basic understanding of these concepts, physical access is giving permissions to on-site locations such as buildings, parks, residential areas and so on. Logical access systems limit the access to resources, such as files, computer systems, software, and data. Lastly network-based access control systems manage and control access to computer networks through authentication and authorization processes.
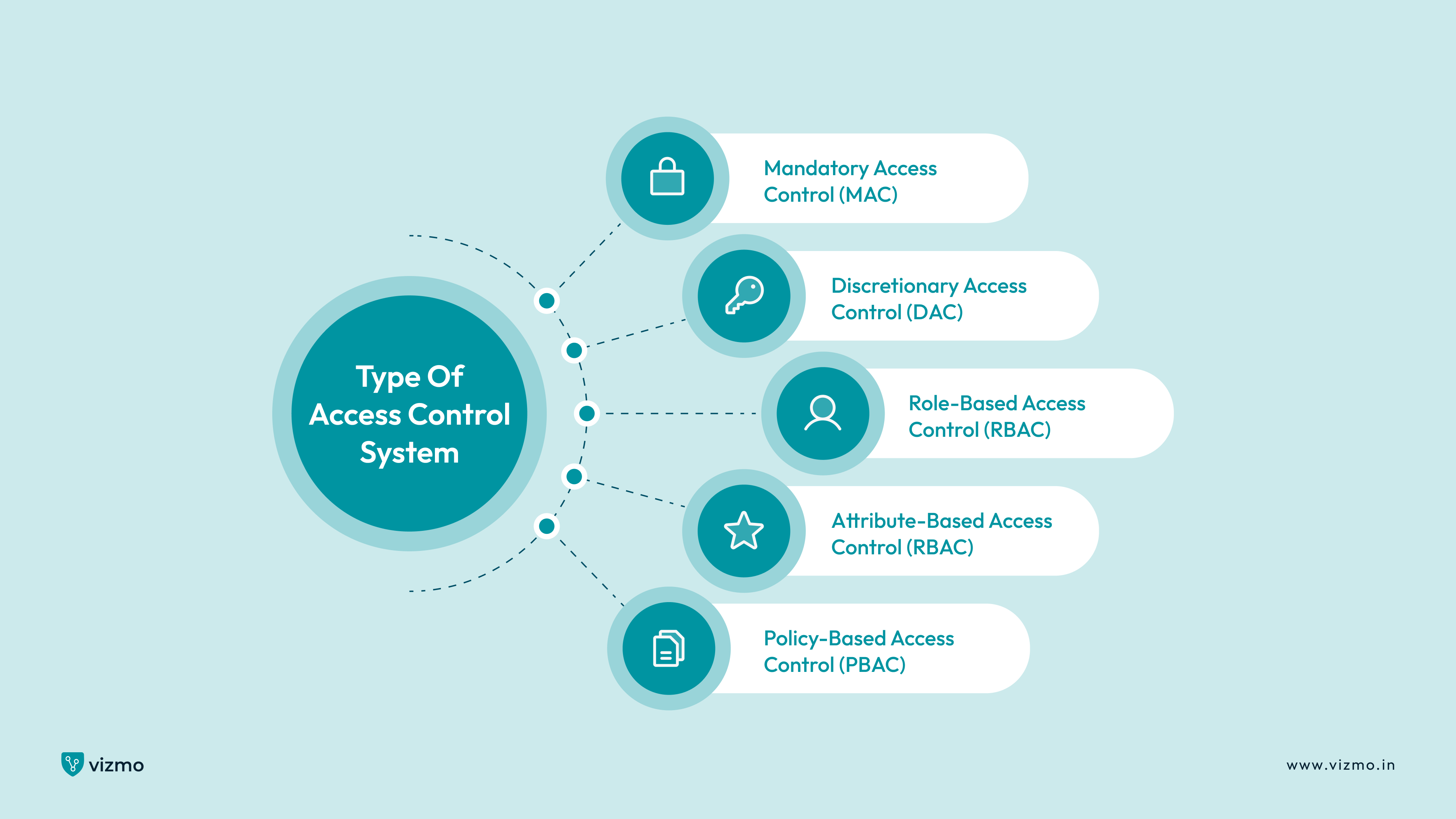
The major types of access control systems include Mandatory Access Control (MAC), Discretionary Access Control (DAC), Role-Based Access Control (RBAC), Attribute-Based Access Control (ABAC), and Policy-Based Access Control (PBAC). These systems offer different degrees of control and flexibility, depending on the security requirements.
Discretionary Access Control (DAC) is the most flexible model and is suitable for small enterprises. Mandatory Access Control (MAC) the mandatory access model is the most restrictive and enforces access based on predefined policies, making it ideal for environments requiring high levels of security. Role-Based Access Control (RBAC) as the name suggests assigns access based on the user's role and is suitable for large organizations with different responsibilities. Attribute-Based Access Control (ABAC) determines access based on attributes (e.g., time, location, role) associated with the user and the resource. This type of model is mostly ideal for dynamic environments like cloud computing. PBAC combines elements of RBAC and ABAC, using policies to make access decisions, making it useful in complex enterprise environments.
AI integration with access models, cloud-based access control systems, biometric access models, Multi-factor authentication, behavioral analytics and zero trust security models are some of the notable emerging trends in the dynamic of access control systems.
Let's explore each access control model in greater detail to gain a clearer understanding of how they work.
1. Mandatory Access Control (MAC)
The Mandatory access control (MAC) model is the most stringent of all access control systems. The MAC system is best suited for enterprises and businesses with high security demands and discretion. MAC enforces access policies through a centralized authority. The model has an administrator given the authority to establish a set of predefined criteria or policies. MAC ensures that the authority of the systems administrator cannot be overruled or circumvented. According to the policies the administrator provides access to users. MAC ensures that the authority of the systems administrator cannot be overruled or circumvented.
MAC is a model that understands the importance of security in the workplace and offers high levels of security as one of its primary advantages. Because of its centrally controlled access policies MAC systems are less prone to breaches and unauthorized access. However, the MAC model is very rigid and lacks flexibility. Any modification to user permissions requires the administrator to adjust the user's access settings throughout the system, not just at a single control point.
2. Discretionary Access Control (DAC)
In terms of flexibility, DAC is the complete contradiction of MAC, being the simplest model among the various types of access control systems. Unlike DAC, MAC has multiple administrators managing and controlling access to various resources. The resource owner or administrator is empowered to determine who can access it and what level of access they can have. For instance, in a personal computer, the owner of a document can decide who else on the network can open, edit, or delete that document.
DAC provides administrators or owners the freedom to share access at their own discretion, without needing approval from a central authority, making it a simple and straightforward procedure. The DAC model is well-suited for residential properties and businesses that have multiple managers.
3. Role-Based Access Control (RBAC)
The Role-Based Access Control (RBAC) model, also known as non-discretionary access control, is a more structured and refined version of the DAC model. RBAC grants access to resources by identifying different roles or specific job titles within an organization. The different roles or identities also determine the level of access a person should be granted.
Role-Based Access Control (RBAC) is rapidly emerging as the most widely adopted access control model, mostly due to its ability to manage permissions, easily assign and grant access based on predefined roles. The model is commonly implemented for corporate and residential properties. Additionally RBAC is also a highly scalable model, making it easier to manage access as organizations or residential areas grow. The only drawback is that it can become complex if not properly managed. In growing organizations, the number of roles can multiply quickly making managing roles and permissions more challenging.
4. Attribute-Based Access Control (ABAC)
In an ABAC model, instead of identifying and providing access through roles, the model grants access by recognizing a variety of attributes. These attributes can include anything from user characteristics, like an employee's job title or department, to environmental conditions such as time of access or location. ABAC is particularly well-suited for complex environments such as cloud computing, healthcare, or large enterprises, where access requirements can vary widely depending on the situation.
Gartner and NIST, along with others, are now considering ABAC as one among the leading approaches for access control going forward. ABAC offers a user-friendly design by providing a simpler way to update user profiles instead of relying on complex technical settings. The only drawback of such a model is that its implementation can be tricky as it requires detailed policy creation, attribute management, and ongoing maintenance.
4. Policy-Based Access Control (PBAC)
The federal government’s National Institute of Standards and Technology (NIST) defines policy-based access control as “a strategy for managing user access to one or more systems, where the business roles of users are combined with policies to determine what access privileges users of each role should have.” Policy-Based Access Control (PBAC) assigns access to resources based on predefined policies that take into account rules, roles, and attributes.
The PBAC model uses a methodology called Policy as Code (PaC), allowing policies to be seamlessly integrated directly into the code. One advantage of a PBAC model is its scalability with an organization’s growth through automation, you can write the policy once, and it automatically handles the rest. The PBAC model is highly recommended for businesses with complex and dynamic access requirements. Although the PBAC model can experience performance overhead in large-scale environments due to real-time evaluation of multiple attributes and policies.
The Future of Access Control Systems
As technology advances, AI integration is rapidly evolving, leading us into a world where tasks are becoming more simplified and automated. According to Precedence Research, the artificial intelligence (AI) market size is projected to grow at a compound annual growth rate (CAGR) of 38.1% from 2022 to 2030. The growing integration of AI is a significant and a revolutionizing development for access control systems, bringing about major changes in how they operate. For instance, AI is much better and accurate at identifying and responding to suspicious behavior in real-time. With the integration of AI in access control models, advancements in biometric recognition, such as facial and voice recognition, gait analysis, and real-time threat recognition are expected to become more precise, ensuring more efficiency and security.
AI integration with access control models also promises to improve the scalability and efficiency of access control systems. By automating routine tasks, optimizing access policies, and processing large volumes of data quickly, AI streamlines operations and adapts to evolving workplace security needs with better versatility.
However, with AI integration, it's crucial to ensure that the access control systems perform transparently and be fully compliant with data protection regulations. AI in access control raises important ethical considerations and potential risks associated with privacy, bias, accountability, emergency scenarios, and global settings.
How Does Access Control Systems Work?
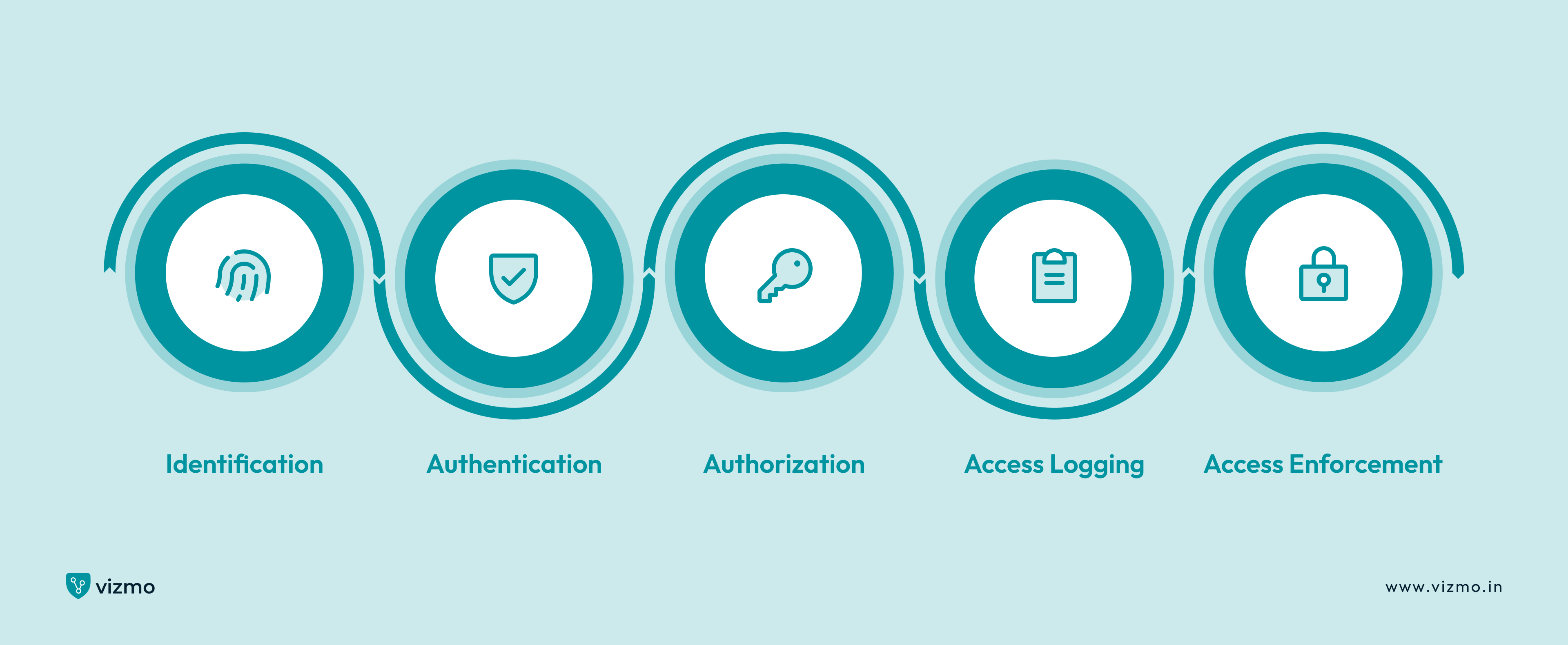
The access control system functions according to pre-established criterias, utilizing unique identifiers such as PINs, usernames, passwords, and other forms of identification. When a user presents their credentials, the system evaluates them to determine if access should be granted. Depending on the specific credentials linked to the user's identifier, the system also controls the timing and extent of access while simultaneously recording the event.
This process involves five key steps: identification, authentication, authorization, access logging and access enforcement.
Identification: Identification is the first step in an access control system, where the system verifies the identity of the individual seeking access using unique credentials like keycards, biometric data, or a PIN.
Authentication: Next, the system processes the identification data against its database to authenticate the individual, confirming whether they are legitimate. Enhanced security measures like two-factor or three-factor authentication can be employed for added protection.
Authorization: Finally, the system checks if the authenticated individual has the necessary permissions for the requested access. If authorized, access is granted; if not, it is denied. This ensures that only those with proper clearance can access restricted areas or sensitive information, completing the process.
Access Logging: Whether access is granted or denied, the system records the event. This log or record typically includes details such as the user's identity, the time of the access attempt, the resource or area accessed, and the outcome (granted or denied). Logging is essential for auditing, monitoring, and ensuring accountability within the system.
Access Enforcement: If access is authorized, the system grants the access by allowing the user to interact with the resource or enter the area. This control is usually handled by things like door locks, software, or network firewalls that are managed by the access control system.
Pros and Cons of Access Control Systems
1. Mandatory Access Control (MAC)
Pros: High security, strict policy enforcement, minimal unauthorized access.
Cons: Inflexible, complex management, limited user control.
2. Discretionary Access Control (DAC)
Pros: Flexible, easy to implement, user autonomy.
Cons: Security risks, inconsistent policies, prone to misconfiguration.
3. Role-Based Access Control (RBAC)
Pros: Scalable, easy management, consistent policies.
Cons: Role proliferation, limited flexibility, complex setup.
4. Attribute-Based Access Control (ABAC)
Pros: Fine-grained control, flexible, context-aware.
Cons: Complex to implement, performance overhead, high maintenance.
5. Policy-Based Access Control (PBAC)
Pros: Flexible policies, scalable, automation-friendly.
Cons: Performance impact, complex management, challenging setup.
Selecting the right access control model for your business is crucial for the efficiency, security of your organization and to simply complete your workplace security checklist. Businesses must choose their access control models keeping in mind the security, flexibility, and complexity the model provides while selecting it. Each of the models come with their own drawbacks and advantages. For instance MAC suits high-security environments but lacks flexibility.
DAC is flexible yet less secure making it ideal for small businesses. RBAC balances scalability and management, effective in large, role-defined organizations though keeping up with role growth is challenging. ABAC provides detailed control in changing environments but can be complicated to manage. The model is best suited for cloud computing, healthcare, or large enterprises. PBAC is ideal for large enterprises but its scalability and implementation is complex.
Implementing Access Control Systems
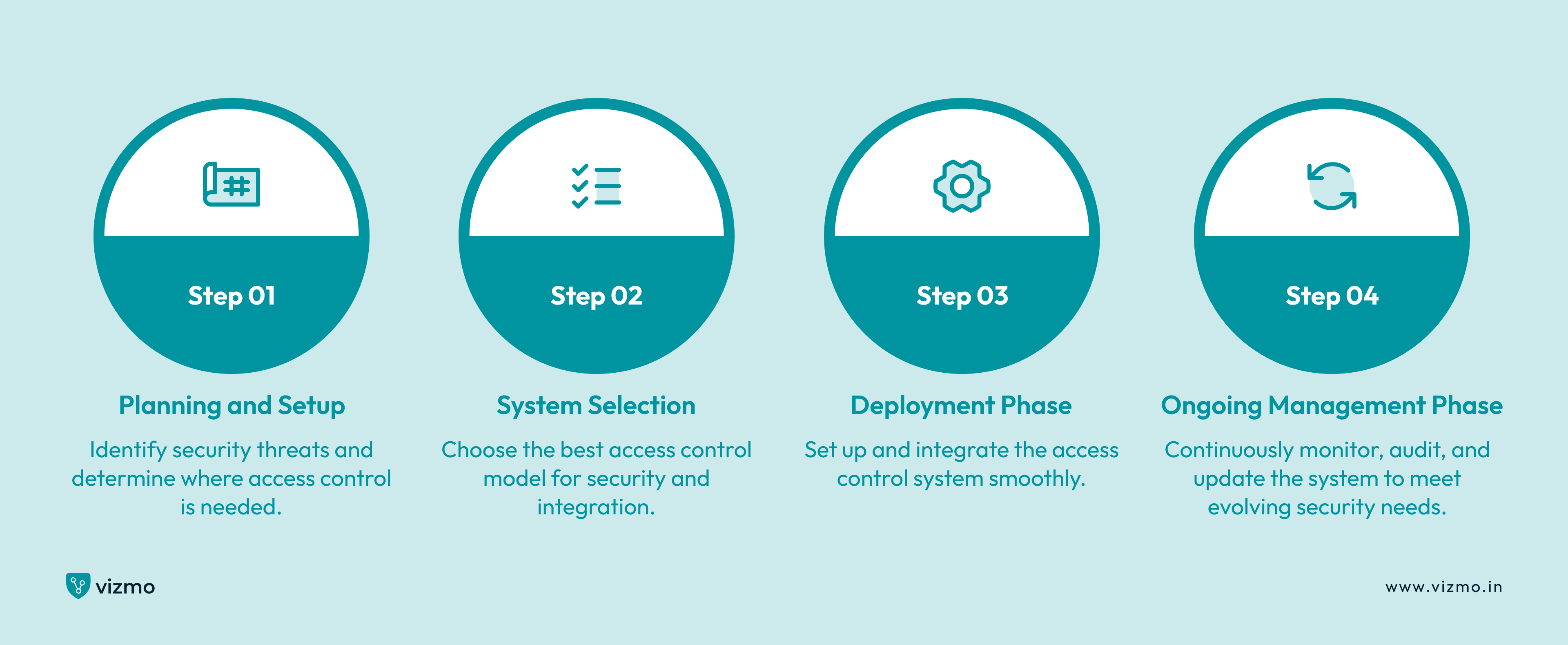
1. Planning and Setup
Begin by identifying potential security threats and vulnerabilities in your organization to determine areas needing strict access control and appropriate security levels. Then, analyze your specific needs by considering factors like the number of users, types of resources to protect, and required access levels for different roles. Evaluate entry points and critical areas to understand daily use, ensuring the access control system integrates smoothly with existing systems like video surveillance, alarms, and IT infrastructure.
2. System Selection
Make informed decisions while selecting the best access control model for your unique requirements. For instance select MAC for high security, DAC for flexibility, RBAC for structured environments, ABAC for dynamic settings or PBAC for policy-driven management.
3. Deployment Phase
The deployment phase in an access control model involves setting up and implementing the necessary configurations and integrations with your existing systems. This includes configuring the system settings, adding users, defining access levels, and customizing the system to meet the specific needs. This step is crucial for ensuring that the access control system runs smoothly and efficiently within your organization.
4. Ongoing Management Phase
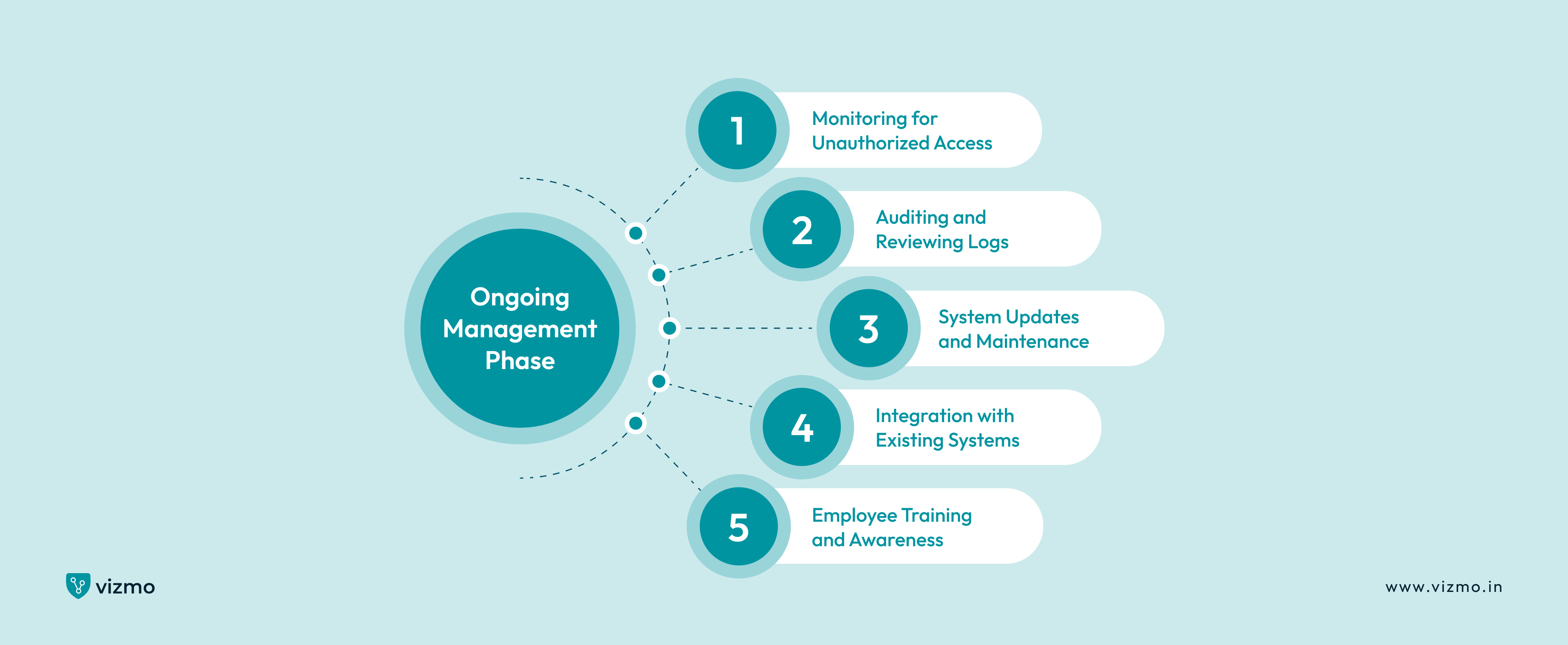
The ongoing management phase involves regular monitoring, auditing, and updating the access control system to address any issues that arise and keep up with evolving security needs. Ongoing management of access control systems includes monitoring for unauthorized access and auditing logs for identifying security issues.
In this phase you need to make sure that your access control model has the ability to seamlessly integrate with your existing systems, including video surveillance systems, alarm systems, IT infrastructure and visitor management systems. Another step would be to make sure your provider is offering regular updates in the system with new features and permissions to keep the system running smoothly with your growing organization. Lastly, training employees and users to make informed decisions is also a crucial aspect of the ongoing management phase.
Here’s how Vizmo can help you in choosing and implementing the right access control system for your business. Vizmo provides a complete access control and office security solution, covering everything from planning to management. Vizmo provides end-to-end support, staying with you even after implementation to assist with ongoing updates and system management.
Final Thoughts
Having an access control model is as we now know is paramount for managing access and protecting valuable resources. However, selecting the right access control model for your specific requirements is just as necessary for effectively protecting your assets and ensuring better workplace security and efficiency.
Before selecting an access control system it is necessary to assess your specific security needs and consult with professionals to ensure your access control system is tailored to your organization's requirements.
Vizmo expertly guides you in selecting and implementing the ideal access control system tailored to your specific and personalized needs. For personalized advice and solutions, book a call with Vizmo.

